In today's digital era, remote IoT (Internet of Things) management has become an essential aspect of modern cloud computing strategies. As businesses increasingly rely on AWS (Amazon Web Services) for their infrastructure needs, understanding how to securely connect to a VPC (Virtual Private Cloud) using SSH (Secure Shell) is critical. This article will explore the intricacies of remote IoT VPC SSH AWS and provide practical insights to help you build robust, secure cloud networking solutions.
Whether you're a developer, system administrator, or IT professional, this guide is designed to equip you with the knowledge and tools necessary to manage remote IoT devices within an AWS environment. From setting up a VPC to configuring SSH connections, we'll cover everything you need to know to ensure your IoT devices remain secure and operational.
As cybersecurity threats continue to evolve, securing IoT devices has never been more important. By leveraging AWS's powerful tools, you can create a secure, scalable, and efficient infrastructure for your IoT projects. This article will walk you through the entire process, step by step, ensuring you have the confidence to implement these solutions effectively.
Read also:What Is The Difference Between Tablet And Ipad A Comprehensive Guide
Table of Contents
- Introduction to RemoteIoT VPC SSH AWS
- Understanding VPC on AWS
- Securing IoT Devices with SSH
- Setting Up a VPC for Remote IoT
- Configuring SSH Access to VPC
- Best Practices for RemoteIoT VPC SSH AWS
- Monitoring and Securing Your VPC
- Troubleshooting Common Issues
- Case Studies of Successful RemoteIoT Implementations
- Conclusion and Next Steps
Introduction to RemoteIoT VPC SSH AWS
The integration of remote IoT devices with AWS infrastructure has revolutionized how businesses manage their operations. A Virtual Private Cloud (VPC) serves as the backbone of this integration, providing a secure and isolated environment for IoT devices. By leveraging SSH, organizations can establish secure connections to their devices, ensuring data integrity and confidentiality.
This section will introduce the fundamental concepts of remote IoT VPC SSH AWS, highlighting its importance in modern cloud computing. We'll also explore the benefits of using AWS for IoT projects, including scalability, flexibility, and robust security features.
Understanding VPC on AWS
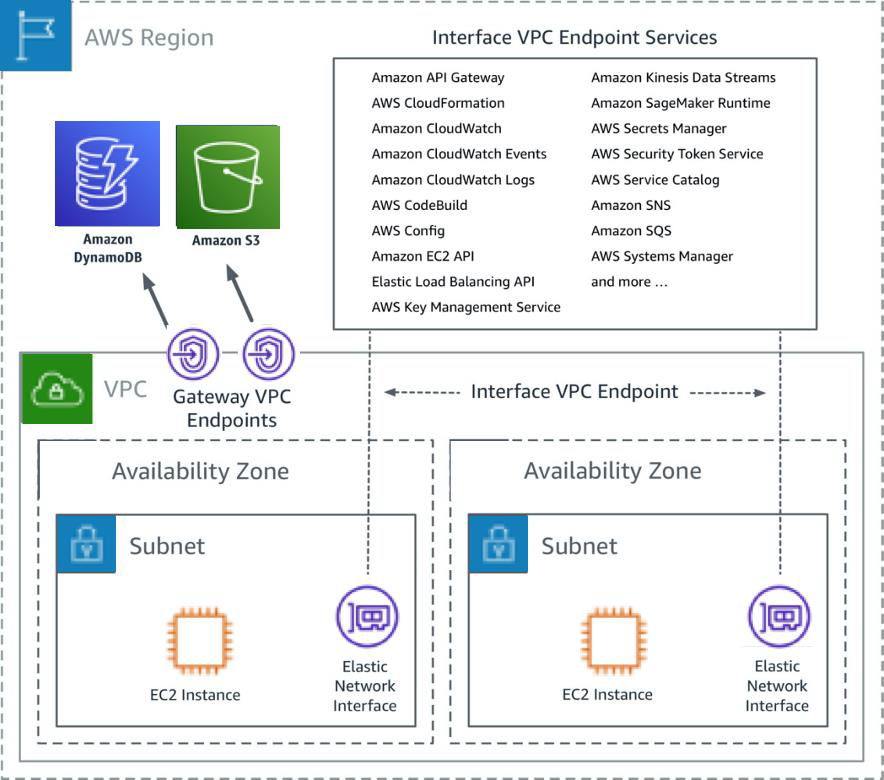
AWS VPC is a foundational component of AWS infrastructure, allowing users to create a logically isolated section of the AWS Cloud. This virtual network closely mirrors traditional data center networks, offering complete control over IP address ranges, subnets, route tables, and network gateways.
By understanding VPC architecture, you can design a secure and efficient network for your IoT devices. This section will delve into the key components of a VPC, such as subnets, internet gateways, and security groups, and explain how they contribute to a robust IoT ecosystem.
Securing IoT Devices with SSH
SSH is a cryptographic network protocol that provides secure communication over unsecured networks. When managing remote IoT devices, SSH ensures that data transmitted between devices and servers remains encrypted and protected from unauthorized access.
In this section, we'll explore the role of SSH in securing IoT devices and discuss best practices for implementing SSH in an AWS environment. We'll also examine common vulnerabilities and how to mitigate them to ensure your IoT infrastructure remains secure.
Read also:The Junior League Empowering Women Through Community Service And Leadership
Setting Up a VPC for Remote IoT
Step 1: Create a VPC
The first step in setting up a VPC for remote IoT is to create a new VPC within your AWS account. This involves defining the IP address range, selecting a CIDR block, and configuring other essential parameters.
Here's a step-by-step guide to creating a VPC:
- Log in to the AWS Management Console
- Navigate to the VPC dashboard
- Click "Create VPC" and enter the required details
Step 2: Configure Subnets
Once your VPC is created, the next step is to configure subnets. Subnets allow you to divide your VPC into smaller segments, enabling you to control traffic flow and improve security.
Key considerations when configuring subnets include:
- Defining public and private subnets
- Assigning IP address ranges
- Configuring route tables and network ACLs
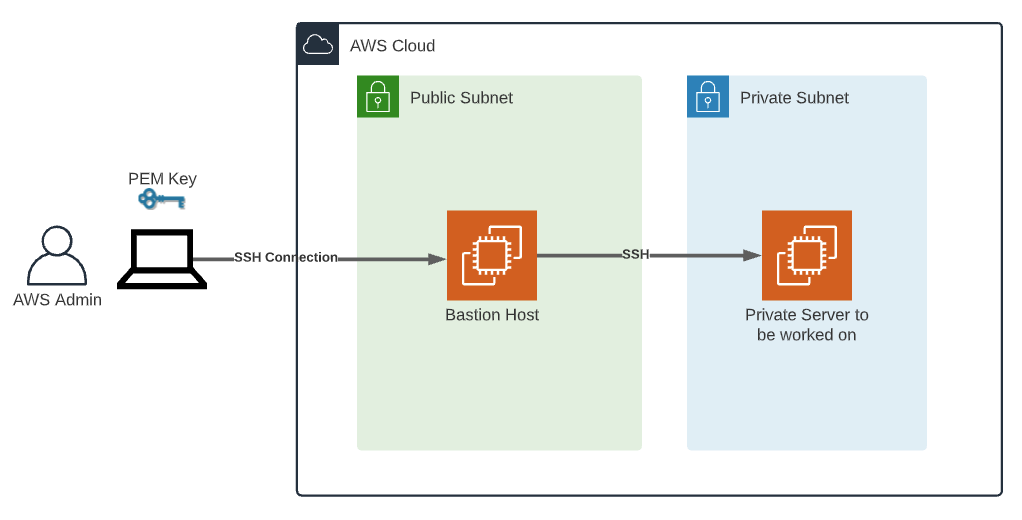
Configuring SSH Access to VPC
Configuring SSH access to your VPC is critical for managing remote IoT devices. This involves setting up security groups, key pairs, and other security measures to ensure only authorized users can access your devices.
In this section, we'll walk you through the process of configuring SSH access, including:
- Creating SSH key pairs
- Setting up security group rules
- Testing SSH connections
Best Practices for RemoteIoT VPC SSH AWS
Use SSH Keys Instead of Passwords
Using SSH keys instead of passwords significantly enhances the security of your IoT devices. SSH keys provide a more secure authentication method, reducing the risk of brute-force attacks and unauthorized access.
To implement SSH keys:
- Create a key pair using the AWS Management Console
- Download the private key and store it securely
- Configure your IoT devices to accept the public key
Limit SSH Access to Specific IPs
Restricting SSH access to specific IP addresses or ranges is another effective way to enhance security. By limiting access to trusted sources, you reduce the likelihood of unauthorized access attempts.
To configure IP restrictions:
- Modify security group rules to allow traffic only from specific IPs
- Test the configuration to ensure it works as expected
Monitoring and Securing Your VPC
Continuous monitoring and proactive security measures are essential for maintaining the integrity of your VPC. AWS provides several tools and services to help you monitor your infrastructure and detect potential threats.
Key tools for monitoring and securing your VPC include:
- AWS CloudTrail for tracking API activity
- AWS Config for monitoring resource changes
- AWS Shield for protecting against DDoS attacks
Troubleshooting Common Issues
Even with the best planning and implementation, issues can arise when working with remote IoT VPC SSH AWS. This section will address common problems and provide solutions to help you troubleshoot effectively.
Common issues include:
- SSH connection errors
- Network connectivity problems
- Security group misconfigurations
Case Studies of Successful RemoteIoT Implementations
To illustrate the practical application of remote IoT VPC SSH AWS, we'll examine real-world case studies of organizations that have successfully implemented these solutions. These case studies will highlight the benefits, challenges, and lessons learned from their experiences.
Examples include:
- A smart city initiative leveraging AWS for IoT device management
- A manufacturing company using remote IoT to optimize production processes
Conclusion and Next Steps
RemoteIoT VPC SSH AWS offers a powerful and secure solution for managing IoT devices in a cloud environment. By following the guidelines and best practices outlined in this article, you can build a robust infrastructure that meets your business needs while ensuring data security and compliance.
As you continue your journey with remote IoT on AWS, consider exploring additional AWS services and tools to enhance your infrastructure. We invite you to share your thoughts and experiences in the comments section below and explore other articles on our site for further insights into cloud computing and IoT technologies.