In today's interconnected world, remote IoT (Internet of Things) management is crucial for businesses and individuals alike. The ability to securely access IoT devices through SSH (Secure Shell) on AWS (Amazon Web Services) provides unparalleled flexibility and control. This article will explore the concept of remote IoT SSH AWS examples, offering valuable insights and practical steps to implement secure remote access solutions.
As technology evolves, the demand for remote IoT management continues to grow. Organizations need robust systems that allow them to monitor, configure, and manage IoT devices from anywhere in the world. AWS, with its powerful infrastructure and security features, is the ideal platform for achieving this goal. This article will guide you through the process, ensuring you have all the tools and knowledge necessary to set up a secure remote IoT environment.
Whether you're a developer, system administrator, or IT professional, understanding how to leverage SSH on AWS for remote IoT access is essential. By the end of this article, you'll have a clear understanding of the best practices, tools, and techniques required to create a secure and efficient remote IoT setup. Let's dive in!
Read also:The Band Cream A Timeless Legacy And Their Impact On Rock Music
Table of Contents
- Introduction to RemoteIoT SSH AWS
- What is SSH and Why Use It?
- AWS Benefits for Remote IoT
- Step-by-Step Setup Process
- Security Best Practices for Remote IoT
- Monitoring and Managing IoT Devices
- Common Issues and Troubleshooting
- Cost Considerations for AWS
- Real-World Use Cases
- Conclusion and Next Steps
Introduction to RemoteIoT SSH AWS
The concept of remote IoT SSH AWS involves using Secure Shell (SSH) protocols to establish secure connections between IoT devices and cloud-based infrastructure provided by Amazon Web Services (AWS). This setup enables users to remotely manage, monitor, and configure IoT devices from virtually anywhere in the world. By leveraging AWS's scalable and secure infrastructure, organizations can ensure that their IoT ecosystems remain robust and protected.
One of the primary advantages of using SSH on AWS for remote IoT access is the enhanced security it provides. SSH encrypts all communication between the client and server, protecting sensitive data from unauthorized access. Additionally, AWS offers a range of security features, such as IAM roles, VPCs, and security groups, which further strengthen the overall security posture of your IoT environment.
What is SSH and Why Use It?
SSH, or Secure Shell, is a cryptographic network protocol used to secure communication between devices over an unsecured network. It provides a secure channel for remote access, file transfers, and command execution. When it comes to remote IoT management, SSH offers several key benefits:
- Encryption: All data transmitted via SSH is encrypted, ensuring confidentiality and integrity.
- Authentication: SSH supports strong authentication methods, such as public-key cryptography, to verify the identity of users and devices.
- Reliability: SSH is widely adopted and trusted, making it a reliable choice for secure remote access.
By using SSH for remote IoT access, organizations can ensure that their IoT devices remain secure and accessible from anywhere in the world.
AWS Benefits for Remote IoT
Amazon Web Services (AWS) offers a range of benefits for remote IoT management, including:
- Scalability: AWS provides a highly scalable infrastructure that can accommodate growing IoT ecosystems.
- Security: With features like IAM roles, VPCs, and security groups, AWS ensures that your IoT devices remain secure.
- Global Reach: AWS's global network of data centers allows for low-latency connections, enabling real-time IoT management from anywhere in the world.
These benefits make AWS an ideal platform for implementing remote IoT SSH solutions.
Read also:Munsters The Beloved Tv Family That Captured Hearts
Step-by-Step Setup Process
Step 1: Create an AWS Account
The first step in setting up a remote IoT SSH AWS example is to create an AWS account. Visit the AWS website and follow the registration process to gain access to the AWS Management Console. Once your account is set up, you can proceed to the next step.
Step 2: Launch an EC2 Instance
After creating your AWS account, the next step is to launch an EC2 instance. EC2 (Elastic Compute Cloud) provides scalable virtual servers that can be used to host your IoT applications and manage remote devices. Follow these steps to launch an EC2 instance:
- Log in to the AWS Management Console.
- Navigate to the EC2 dashboard and click "Launch Instance."
- Select an appropriate AMI (Amazon Machine Image) and instance type for your IoT application.
- Configure instance details, such as the number of instances and network settings.
- Set up storage and add tags as needed.
- Configure security groups to allow SSH access.
- Review and launch your instance, downloading the key pair for secure access.
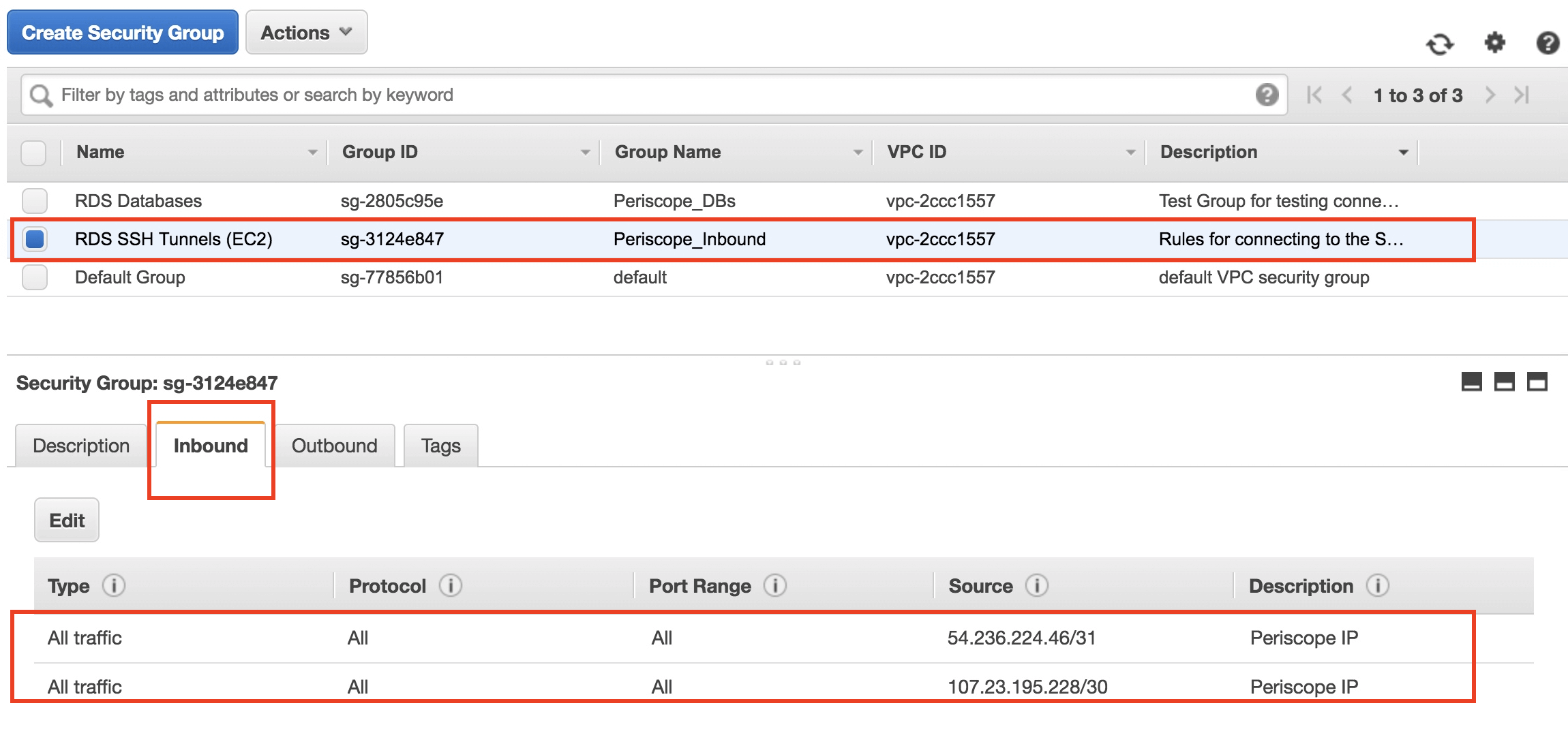
Step 3: Configure Security Groups
Security groups act as virtual firewalls for your EC2 instances, controlling inbound and outbound traffic. To enable SSH access, you'll need to configure your security group to allow traffic on port 22. Follow these steps:
- Go to the EC2 dashboard and select "Security Groups" from the left-hand menu.
- Create a new security group or edit an existing one.
- Add a rule to allow inbound traffic on port 22 (SSH).
- Specify the source IP address or range that will be allowed to access your instance.
- Save your changes and apply the security group to your EC2 instance.
Security Best Practices for Remote IoT
When implementing remote IoT SSH AWS solutions, it's essential to follow security best practices to protect your devices and data. Here are some key recommendations:
- Use Strong Passwords: Ensure that all user accounts have strong, unique passwords.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security by requiring 2FA for SSH access.
- Regularly Update Software: Keep your IoT devices and server software up to date to protect against vulnerabilities.
- Monitor Logs: Regularly review system logs to detect and respond to potential security threats.
By following these best practices, you can significantly reduce the risk of security breaches in your remote IoT environment.
Monitoring and Managing IoT Devices
Effective monitoring and management are crucial for maintaining a healthy and secure IoT ecosystem. AWS offers several tools and services to help you monitor and manage your IoT devices, including:
- AWS IoT Core: A managed cloud service that allows you to connect, monitor, and manage IoT devices at scale.
- CloudWatch: A monitoring service that provides insights into the performance and health of your IoT devices and applications.
- Systems Manager: A service that helps you manage and automate tasks for your EC2 instances and IoT devices.
By leveraging these tools, you can ensure that your IoT devices remain secure, efficient, and reliable.
Common Issues and Troubleshooting
While implementing remote IoT SSH AWS solutions, you may encounter some common issues. Here are a few troubleshooting tips:
- Connection Issues: Ensure that your security groups allow SSH access and that your key pair is correctly configured.
- Performance Problems: Monitor your EC2 instance's resource usage and consider upgrading to a larger instance type if necessary.
- Security Alerts: Investigate any unusual activity in your system logs and take appropriate action to address potential threats.
By addressing these issues promptly, you can maintain a stable and secure remote IoT environment.
Cost Considerations for AWS
While AWS offers a range of benefits for remote IoT management, it's essential to consider the costs involved. AWS pricing is based on a pay-as-you-go model, with charges for EC2 instances, data transfer, and other services. To manage costs effectively:
- Monitor Usage: Use AWS Cost Explorer to track your resource usage and identify areas for optimization.
- Use Reserved Instances: Consider purchasing reserved instances for predictable workloads to save money.
- Optimize Resources: Regularly review and adjust your resource configurations to ensure you're using the most cost-effective options.
By carefully managing your AWS resources, you can keep costs under control while maintaining a robust remote IoT setup.
Real-World Use Cases
Remote IoT SSH AWS solutions have numerous real-world applications, including:
- Smart Agriculture: Farmers can remotely monitor and manage IoT sensors and devices to optimize crop yields.
- Industrial Automation: Manufacturers can use remote IoT access to maintain and troubleshoot equipment in real time.
- Smart Cities: Municipalities can leverage IoT devices to improve traffic management, energy efficiency, and public safety.
These use cases demonstrate the versatility and value of remote IoT SSH AWS solutions in various industries.
Conclusion and Next Steps
In conclusion, remote IoT SSH AWS examples provide a powerful and secure way to manage IoT devices from anywhere in the world. By following the steps and best practices outlined in this article, you can set up a robust and efficient remote IoT environment. To further enhance your knowledge and skills:
- Explore additional AWS services and features to expand your IoT capabilities.
- Stay informed about the latest trends and developments in IoT and cloud computing.
- Engage with the AWS community to learn from others and share your experiences.
We invite you to leave a comment, share this article with your network, or explore other resources on our site. Together, let's build a more connected and secure future with remote IoT SSH AWS solutions!